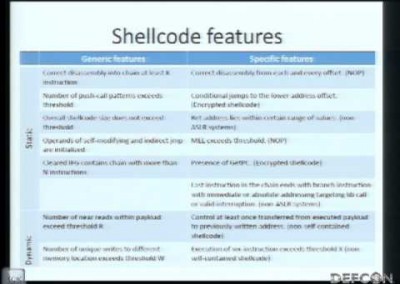
Observe, Hack, Make. A five day outdoor international camping festival for hackers and makers, and those with an inquisitive mind.
It is a four year tradition in The Netherlands to hold such an event. In the spirit of WTH, HIP and HAR the latest edition, OHM2013, is a non-commercial community run event. The event happens thanks to the volunteers, all 3000 of them. They will run the network, help people around the site, give talks, hold workshops and be excellent to one another.
The target audience includes free-thinkers, philosophers, activists, geeks, scientists, artists, creative minds and a whole bunch of people interested in lots of interesting stuff.
Conference information
Location
Geestmerambacht
Koedijk
The Netherlands
Conference program
The conference program can be viewed here.
Articles
Observe, Make, Hack: reflections on a hacker camp
14-08-2014 | Wandering around the paddocks on the first night of camp, the laser lights and smoke in an empty space known as Rainbow Island at the edge of the camp caught my attention.
“A bit sad isn’t it? That huge space, filled with lights and nobody dancing …”, I said. Hacktivist Jason Gulledge paused beside me before answering: “Imagine it as a practice run. We all live in our dreams of what could be.” Read more
My privacy by design talk at OHM 2013
05-08-2014 | This talk is about the possible conflict between getting your message out there, and trying to maintain your site visitor’s privacy. This talk will highlight some of the issues that need to be taken into consideration when building websites for whistleblowers with high security & privacy needs. Read more
NSA power doubles every 4 years – Assange
31-07-2014 | The world is witnessing the creation of a new world order that involves the security state apparatus as an overwhelming force, Julian Assange said during his speech at OHM2013 Observe, Hack, Make conference. Read more