Main category
Subcategory
Main category
Information security & security management
Subcategory
Database
Knowledge is the life of the mind
What is SQL injection?
A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application.
A successful SQL injection exploit can:
- read sensitive data from the database
- modify database data (Insert/Update/Delete)
- execute administration operations on the database (such as shutdown the DBMS)
- recover the content of a given file present on the DBMS file system
- in some cases issue commands to the operating system

White hats publish DDoS hijacking manual, turn tables on attackers
A handful of command-line strings, the open-source penetration-testing tool SQLMap, and knowledge of a command server’s location are pretty much all that’s required to gain access to its back-end database and server-side configuration files.
What is sqlmap?
SQL Injection prevention cheat sheet
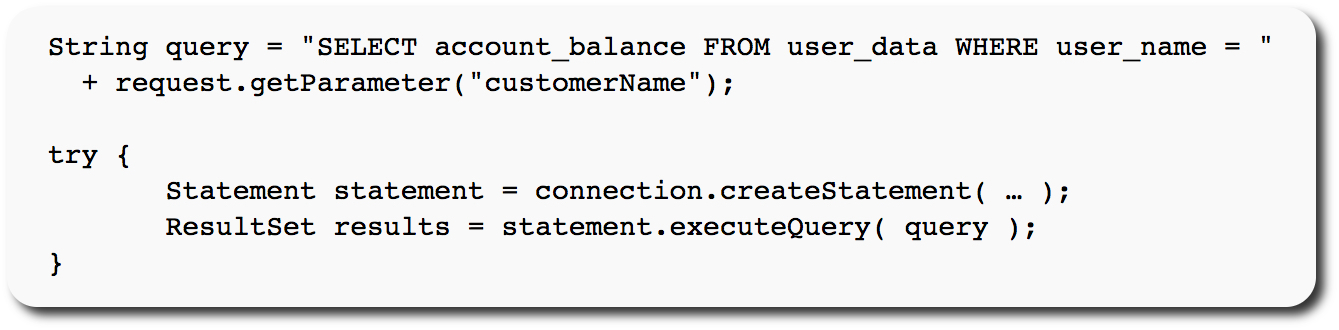
The following (Java) example is UNSAFE, and would allow an attacker to inject code into the query that would be executed by the database.
The unvalidated “customerName” parameter that is simply appended to the query allows an attacker to inject any SQL code they want.
Unfortunately, this method for accessing databases is all too common.
The mystery of Sqlmap’s empty files
Date: 05-12-2014
Source: Will Hack For SUSHI
Can hacks become hackers? What I learned exploiting websites with pros
Date: 16-10-2014
Source: The Guardian
Advanced sqlmap
Date: 10-07-2014
Source: Infosec Institute
Sqlmap Tricks for Advanced SQL Injection
Date: 30-12-2013
Source: Trustwave
Automated audit using SQLMap
Date: 22-01-2013
Source: OWASP
Exploiting a tricky SQL injection with sqlmap
Source: Pentestmonkey
Heuristic methods used in sqlmap
Date: 19-09-2013
Source: Slideshare – Miroslav Stampar
SQL injection: Not only AND 1=1
Date: 26-06-2009
Source: Slideshare – Bernardo Damele A. G.
Advanced SQL injection to operating system full control
Date: 16-04-2009
Source: Slideshare – Bernardo Damele A. G.
How to exploit a POST SQL injection using sqlmap
Date: 15-02-2015
Source: WonderHowTo
Use sqlmap SQL injection to hack a website and database in Kali Linux
Date: 28-08-2014
Source: darkMORE Ops
Using SQL injection vulnerabilities to dump your database
Date: 05-11-2013
Source: jOOQ
Sqlmap tutorial for beginners – hacking with sql injection
Date: 08-08-2012
Source: BinaryTides
Bypassing web application firewalls with SQLMap tamper scripts
Date: 26-08-2011
Source: Websec
Website Hacking – SQL Injections – Sqlmap Introduction
Date: 18-10-2013
Source: YouTube – NetSecNow
Data retrieval over DNS in SQL injection attacks
Date: 30-05-2012
Source: Slideshare – Miroslav Stampar
Advanced SQL injection to operation system full control
Date: 10-04-2009
Source: BlackHat