Photo credit: Christiaan Colen – Flickr
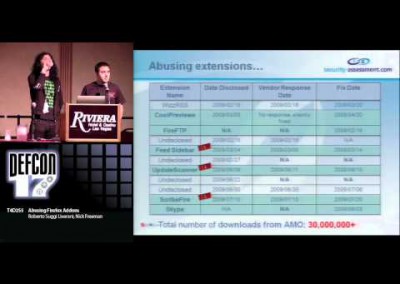
The rise of 2D barcodes started to put them into customer hands as authentication, authorization, payment method and other arbitrary data transport. The implicit trust in them is enormous.
Felix Lindner gives a very quick intro into barcodes and then proceeds to review the contents of selected samples, including their usage in the real world.
The rise of 2D barcodes started to put them into customer hands as authentication, authorization, payment method and other arbitrary data transport. The implicit trust in them is enormous.
Felix Lindner gives a very quick intro into barcodes and then proceeds to review the contents of selected samples, including their usage in the real world.
About the speaker
Felix ‘FX’ Lindner is the technical and research lead of Recurity Labs with 18 years computer technology experience. He possesses a vast knowledge of computer sciences, telecommunications and software development.
His background includes managing and participating in a variety of projects with a special emphasis on security planning, implementation, operation and testing using advanced methods in diverse technical environments.
Connect
About the speaker
Felix ‘FX’ Lindner is the technical and research lead of Recurity Labs with 18 years computer technology experience. He possesses a vast knowledge of computer sciences, telecommunications and software development.
His background includes managing and participating in a variety of projects with a special emphasis on security planning, implementation, operation and testing using advanced methods in diverse technical environments.

Resources
Barcode attack technique (Badbarcode)
The concept of using barcode to launch attack is raised years ago, but no one digs deep. By using SQL barcode, it’s able to launch SQL injection, XSS and overflow attack. Read more
One BadBarcode Spoils Whole Bunch
“We do not know what the bad guys might do. BadBarcode can execute any commands in the host system, or [implant] a Trojan,” said Yang Yu. Read more
What’s in a Boarding Pass Barcode? A Lot
Two-dimensional barcodes and QR codes can hold a great deal of information, and the codes printed on airline boarding passes may allow someone to discover more about you, your future travel plans, and your frequent flyer account. Read more
Resources
Barcode attack technique (Badbarcode)
The concept of using barcode to launch attack is raised years ago, but no one digs deep. By using SQL barcode, it’s able to launch SQL injection, XSS and overflow attack. Read more
One BadBarcode Spoils Whole Bunch
“We do not know what the bad guys might do. BadBarcode can execute any commands in the host system, or [implant] a Trojan,” said Yang Yu. Read more
What’s in a Boarding Pass Barcode? A Lot
Two-dimensional barcodes and QR codes can hold a great deal of information, and the codes printed on airline boarding passes may allow someone to discover more about you, your future travel plans, and your frequent flyer account. Read more