24C3: Cybercrime 2.0
Speaker: Thorsten Holz
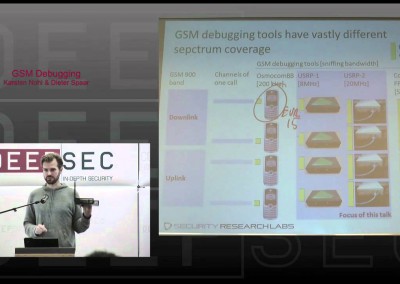
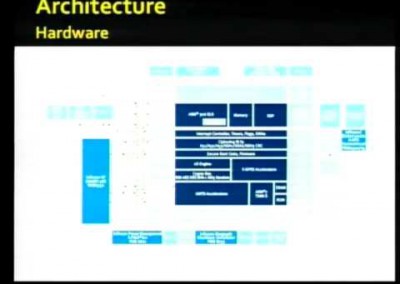
The first part of the talk provides a brief history of Storm Worm (Peacomm, Nuwar, Zhelatin, …), focusing on the actual propagation phase. Afterwards, we describe the network communication of the bot in detail and show how we can learn more about the botnet.
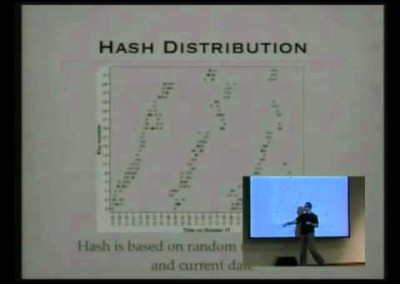
We were able to infiltrate and analyze in-depth the peer-to-peer network used by Storm Worm and present some measurement results.