Photo credit: Christiaan Colen – Flickr
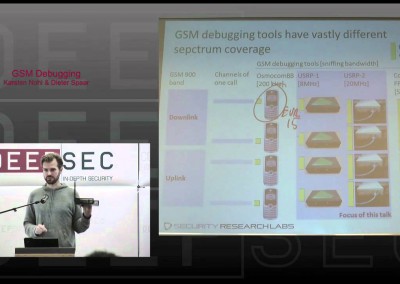
Rootkits are a class of malware which are dedicated to hiding the attacker’s presence on a compromised system. This talk, given by Xeno Kovah, will focus on understanding how rootkits work and what tools can be used to help find them.
This talk will be a very hands-on class about specific techniques which rootkits use and show how a proof of concept rootkit is able to hide things from a defender.
Download the class materials here.
Rootkits are a class of malware which are dedicated to hiding the attacker’s presence on a compromised system. This talk, given by Xeno Kovah, will focus on understanding how rootkits work and what tools can be used to help find them.
This talk will be a very hands-on class about specific techniques which rootkits use and show how a proof of concept rootkit is able to hide things from a defender.
Download the class materials here.
About the speaker
Xeno Kovah’s speciality area is stealth malware and its ability to hide from security software and force security software to lie.
To combat such attacks he researches trusted computing systems that can provide much stronger security guarantees than normal COTS. He co-founded LegbaCore in 2014 to help improve security at the foundation of computing systems.
He is also the founder and lead contributor to OpenSecurityTraining.info.
Connect
About the speaker
Xeno Kovah’s speciality area is stealth malware and its ability to hide from security software and force security software to lie.
To combat such attacks he researches trusted computing systems that can provide much stronger security guarantees than normal COTS. He co-founded LegbaCore in 2014 to help improve security at the foundation of computing systems.
He is also the founder and lead contributor to OpenSecurityTraining.info.

Resources
RootKits 101 (I). The Basics
In this series we are going to look into kernel mode rootkits. Those are the most common ones, and will give us enough fun to be busy for a while. Read more
Linux Rootkits 101
This post is going to be part of a three part series evolving the rootkit to modern/appropriate standards of rootkits for Linux today. Read more
Writing Cisco IOS Rootkits
This paper is about the work involved in modifying firmware images with the test case focused on Cisco IOS. Read more
Resources
RootKits 101 (I). The Basics
In this series we are going to look into kernel mode rootkits. Those are the most common ones, and will give us enough fun to be busy for a while. Read more
Linux Rootkits 101
This post is going to be part of a three part series evolving the rootkit to modern/appropriate standards of rootkits for Linux today. Read more
Writing Cisco IOS Rootkits
This paper is about the work involved in modifying firmware images with the test case focused on Cisco IOS. Read more