DEF CON 20: Demorpheus: Getting rid of polymorphic shellcodes in your network
Speakers: Svetlana Gaivoronski | Dennis Gamayunov
One of the most effective techniques used in CTF is the usage of various exploits, written with the help of well-known tools or even manually during the game.
Experience in CTF participation shows that the mechanism for detecting such exploits is able to significantly increase the defense level of the team.
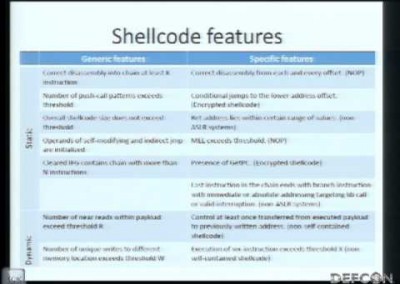
In this presentation we propose an approach and hybrid shellcode detection method, aimed at early detection and filtering of unknown 0-day exploits at the network level.