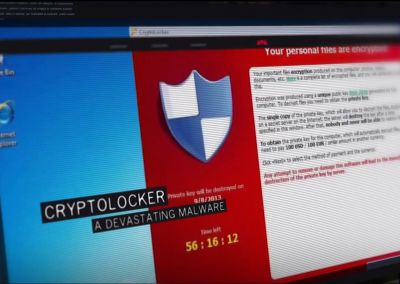
How to pick a proper password
Photo Credit: Christiaan Colen – Flickr
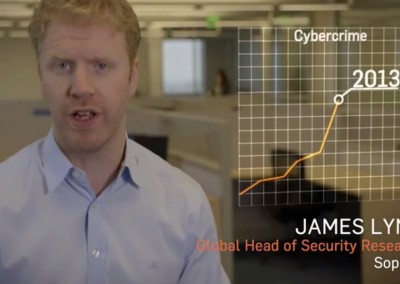
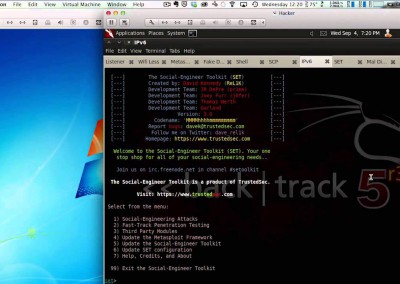
We show you how to pick a proper password and we explain why it’s worth it.
Related videos
Related videos
Videos from the same category or videos related to the subject.
You will find something new to watch and expand your knowledge.