Photo Credit: Christiaan Colen – Flickr
Chris Domas is a cybersecurity researcher, operating on what’s become a new front of war, “cyber.”
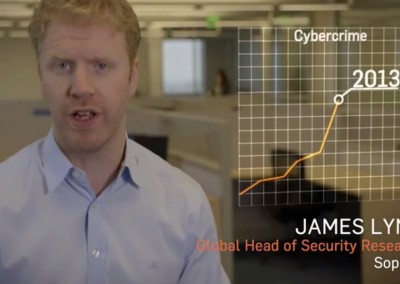
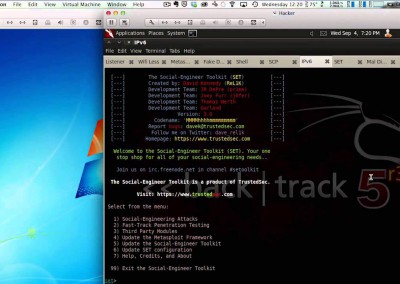
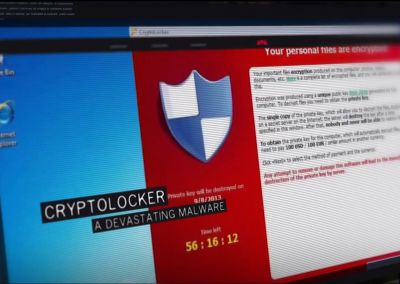
He shows how researchers use pattern recognition and reverse engineering to understand a chunk of binary code whose purpose and contents they don’t know.
Chris Domas is a cybersecurity researcher, operating on what’s become a new front of war, “cyber.”
He shows how researchers use pattern recognition and reverse engineering to understand a chunk of binary code whose purpose and contents they don’t know.