Photo credit: Christiaan Colen – Flickr
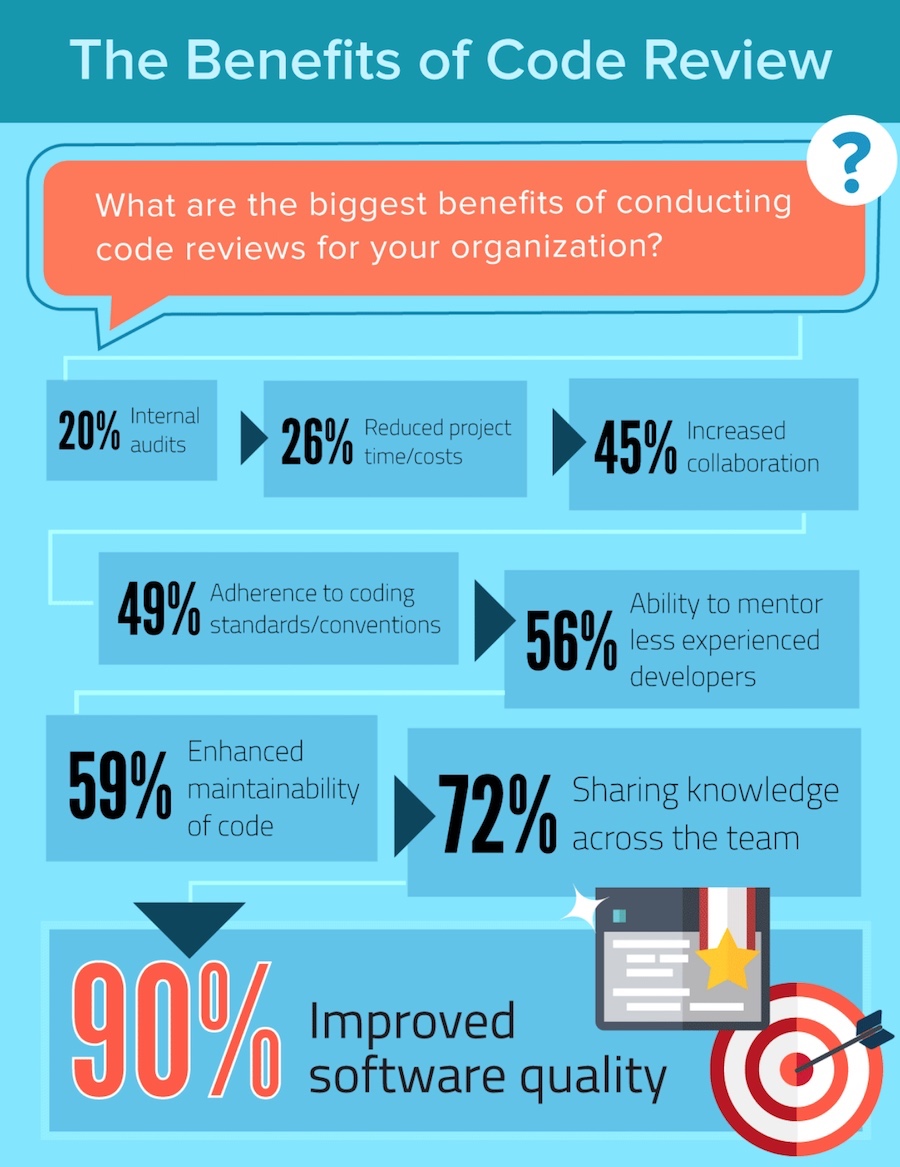
Secure code review is one of the best ways to uncover vulnerabilities and reduce risk of online web applications being breached. However, secure code review has always been challenged as being skill and tools intensive.
But what if this could be simplified so developers on your team could perform it? What if this could be achieved with minimal impact on deadlines?
During this presentation Sherif Koussa will delve into the science and process behind secure code review.
Secure code review is one of the best ways to uncover vulnerabilities and reduce risk of online web applications being breached. However, secure code review has always been challenged as being skill and tools intensive.
But what if this could be simplified so developers on your team could perform it? What if this could be achieved with minimal impact on deadlines?
During this presentation Sherif Koussa will delve into the science and process behind secure code review.
About the speaker
Sherif Koussa is an Application Security Consultant at Software Secured. Sherif has 11 years of professional experience. After years of software development and project management, Sherif specialized in application security.
He is part of SANS GSSP.NET and GSSP.Java steering committees and an exam development consultant for GIAC.
Sherif has done security code reviews for major financial institutions and high profile governmental departments.
Connect
About the speaker
Sherif Koussa is an Application Security Consultant at Software Secured. Sherif has 11 years of professional experience. After years of software development and project management, Sherif specialized in application security.
He is part of SANS GSSP.NET and GSSP.Java steering committees and an exam development consultant for GIAC.
Sherif has done security code reviews for major financial institutions and high profile governmental departments.

Resources
11 proven practices for more effective, efficient peer code review
These 11 proven practices for efficient, lightweight peer code review are based on a study at Cisco Systems using SmartBear CodeCollaborator. They can help you ensure that your reviews both improve your code and make the most of your developers’ time. Read more
What to look for in a Code Review
The aim of this article is to outline just some of the things a reviewer could be looking out for when performing a code review. Read more
Code review workflow
The workflow was built around Beanstalk’s Code Review tools that make it super easy to conduct code reviews and ship better quality projects to your users. Read more
Resources
OWASP Code Review Guide Project
This guide focuses on the mechanics of reviewing code for certain vulnerabilities, and provides limited guidance on how the effort should be structured and executed. Read more
5 Best Practices for the Perfect Secure Code Review
Secure code review is the process organization’s go through to identify and fix potentially risky security vulnerabilities in the late stages of the development process. As the last threshold before an app is released, secure code reviews are an integral part of the security process. Read more
11 proven practices for more effective, efficient peer code review
These 11 proven practices for efficient, lightweight peer code review are based on a study at Cisco Systems using SmartBear CodeCollaborator. They can help you ensure that your reviews both improve your code and make the most of your developers’ time. Read more
What to look for in a Code Review
The aim of this article is to outline just some of the things a reviewer could be looking out for when performing a code review. Read more
Code review workflow
The workflow was built around Beanstalk’s Code Review tools that make it super easy to conduct code reviews and ship better quality projects to your users. Read more